Trump Campaign Site Hacked – What We Know & Lessons Learned
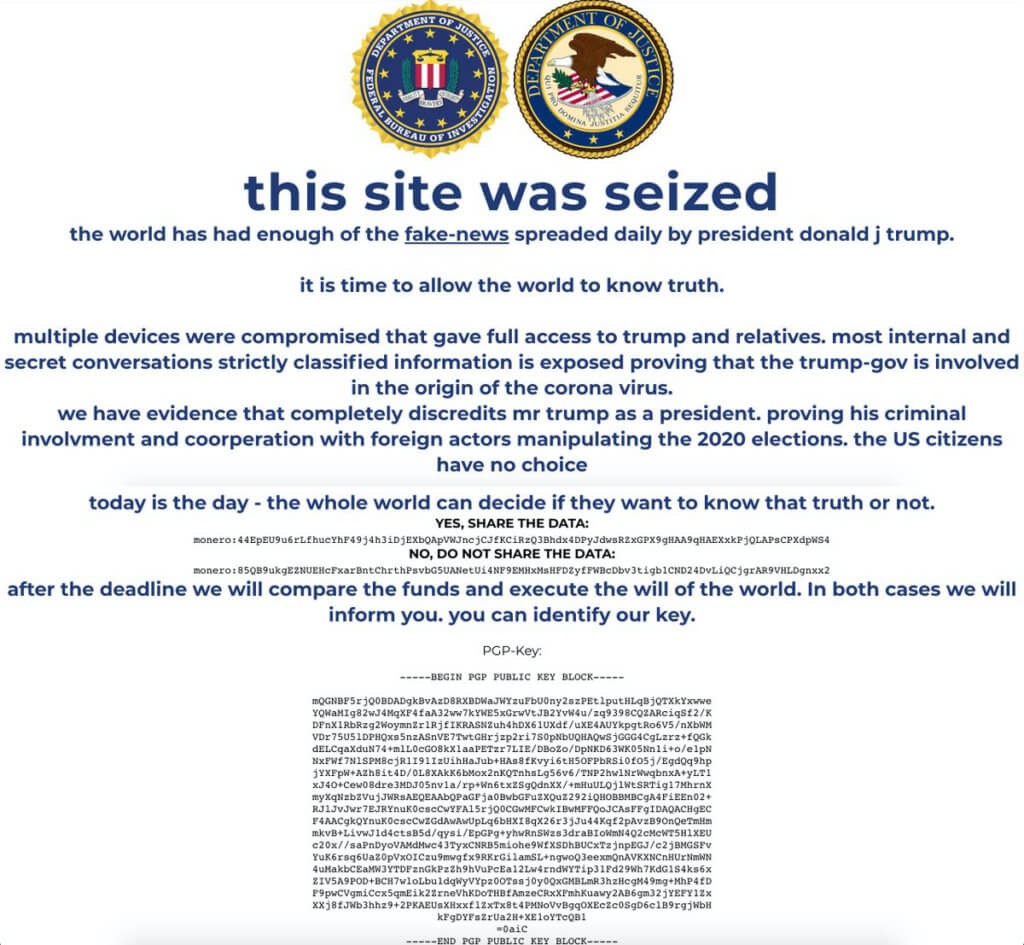
On October 27, 2020 at approximately 4:50pm Mountain Time, Donald Trump’s campaign website, www.donaldjtrump.com, was defaced. The attackers left a message claiming they had compromising information on President Trump. The defacement page contained two Monero cryptocurrency wallet IDs encouraging visitors to “vote” by sending cryptocurrency to the wallets, indicating that if the first wallet received more money than the second wallet, the attackers would release this compromising information.
While the site was compromised, visitors were greeted with the following:
Wordfence protects WordPress websites, and we offer a hacked site cleaning service for WordPress site owners. Donald Trump’s campaign website is hosted using Expression Engine, which is an alternative content management system to WordPress. While Wordfence doesn’t protect sites using Expression Engine, we thought we’d take a look at the facts surrounding this incident and what lessons we might learn.
Technical Analysis
The campaign website made use of the Expression Engine CMS, a commercial CMS with few known vulnerabilities. The site used Cloudflare as a content delivery network (CDN).
Since the site was protected by Cloudflare, the attackers would not have been able to access the site via FTP or SSH unless they knew the Origin IP, that is, the IP of the server hosting the site. When a site uses Cloudflare, the Cloudflare servers are what site visitors access, rather than the ‘origin’ server that actually contains the content and any web application. Cloudflare tries to hide the origin server IP address, making it difficult to access that server unless you can discover the IP address.
The defacement page itself displayed two XMR (Monero) wallets. Monero is a cryptocurrency popular amongst threat actors because it uses an obfuscated public ledger. This means that, while transactions are recorded, they’re not currently traceable. This makes it impossible for outsiders to discover who sent money to each wallet or the amounts involved.
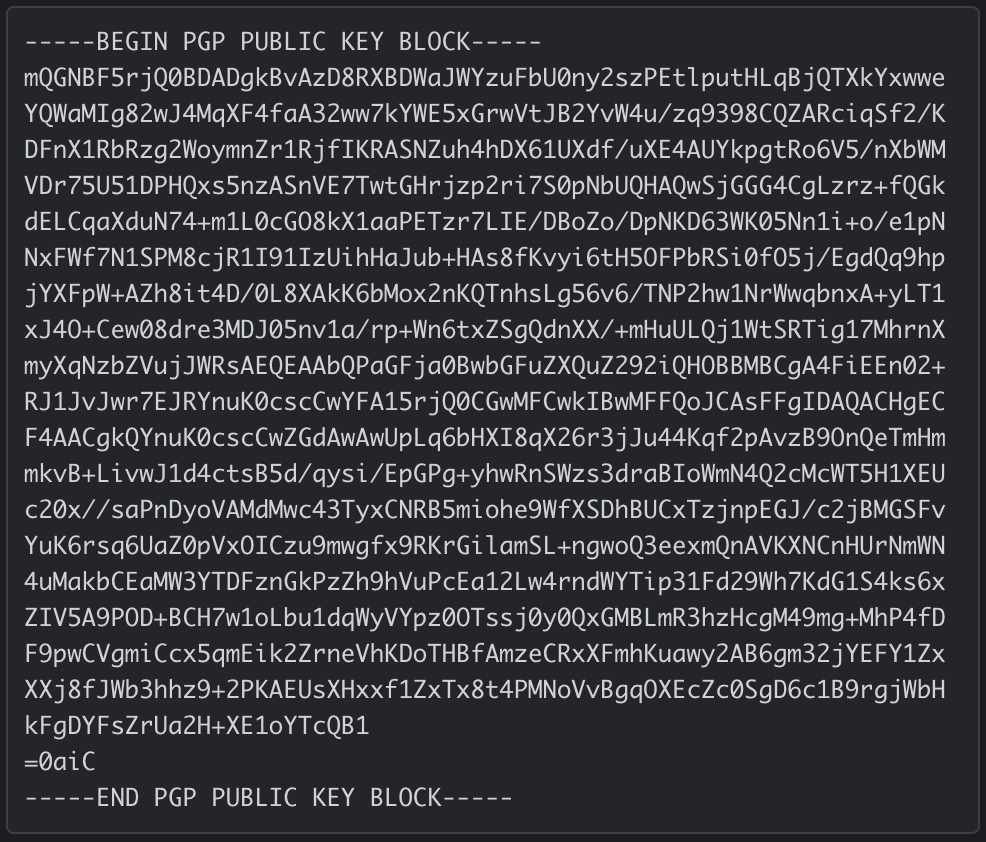
The attackers also left a Pretty Good Privacy(PGP) Public Key on the defacement page. A PGP Public Key can be used to verify signed messages and ensure that a message sender is the same person who posted the public key. If the attackers later decided to release information, they could prove they were the same threat actors who defaced the site by signing released information with their private key.
Only information signed with their private key would be verifiable using the published public key. In this case, the Public Key appears to correspond to a nonexistent email address, hack@planet.gov. Nonetheless, we have provided the PGP key for posterity:
Potential Intrusion Vectors(IVs)
There are several possible intrusion vectors, or mechanisms that the attackers could have used to gain access and deface the Trump campaign website. We describe several possibilities below, but to be clear, without forensic evidence to verify these theories, we cannot definitively know how the site was compromised.
In each case, compromised credentials are by far the most probable Intrusion Vector. A Dutch Researcher recently claimed to have accessed Trump’s Twitter account using the password “maga2020!”. Trump’s Twitter account was also hacked In 2016 when a data breach revealed that he was using the password “yourefired”.
IV: Compromised credentials used to sign into Expression Engine – High Probability
Expression Engine, like most content management systems, provides an administrative panel for publishing content. By default this is located at /admin.php. On donaldjtrump.com, however, the admin login has been relocated to a different location, an example of security through obscurity.
The Internet Archive indicates that the last time the admin page was accessible in the default location was in June of 2015. Even in this hidden location, if an attacker was able to access the administrative panel they would have been able to alter any content on the site, though they would not have had access to any sensitive information.
The “Privacy Policy” and “Terms & Conditions” pages are displaying a “404 page not found” error hours after the site has been restored. This indicates that something changed on the content management system itself, rather than on the Cloudflare configuration. So we believe that the CMS being compromised is therefore a higher probability than Cloudflare being compromised, which we describe below.
IV: Compromised credentials used to sign into Cloudflare – Medium Probability
If an attacker was able to sign into the campaign’s Cloudflare account, they could have pointed the domain to an IP address under their control, effectively replacing the site’s content with the content on their own hosting account. This might also explain how the campaign was able to “restore” the original site content so quickly.
Simply pointing the domain back to the correct IP would have reverted the defacement. The fact that some pages on the site, such as the “Privacy Policy” and the “Terms of Service” are still displaying 404 errors at the time of our publication indicates that this is a less likely intrusion vector.
IV: Compromised Credentials or Social Engineering used to change domain nameservers at registrar – Low Probability
This would work using a similar mechanism to the Cloudflare compromise. If an attacker was able to login to the account where the domain donaldjtrump.com was registered, or socially engineer their way into the account at the domain’s registrar, they might have been able to point it away from Cloudflare’s nameservers and to nameservers under their control.
The fact that some pages on the site are still displaying 404 errors indicates that this is a less likely possibility. Additionally, nameserver changes typically take long enough to propagate that the defaced page would likely still be visible from some locations.
IV: Origin server hacked via FTP or SSH – Low Probability
This is the least likely scenario since the attackers would need to know the site’s origin IP address as well as the FTP or SSH credentials for the site’s hosting account in order to connect directly to the site without being blocked by Cloudflare.
IV: Web Application Vulnerability – Low Probability
While it is possible that a vulnerability in Expression Engine was exploited, Expression Engine has had few known vulnerabilities and the chances of a 0-day vulnerability in this CMS remaining unknown for long are low. Additionally, a vulnerability or exploit chain would be required to allow privilege escalation or remote code execution in order for the attacker to deface the site in this manner.
Takeaway Lessons
Almost every possible scenario includes reused credentials being exploited to gain access to the donaldjtrump.com site. In almost every case, having 2-Factor Authentication enabled would have prevented such a scenario from occurring. It’s also a reminder that it is important to enable 2-Factor Authentication not only on your website’s administrative panel, but on every service that offers it, including services you might not think of as being vulnerable.
If the credentials you are using have been exposed in a data breach, it doesn’t matter how secure the service you’re using is. By enabling 2-Factor Authentication, you add an extra layer of protection.
While Wordfence doesn’t offer protection for Expression Engine, we do offer best-in-class protection for WordPress. This includes 2-Factor Authentication as a completely free feature.
Don’t wait for an attacker to guess your password. Turn on 2-Factor Authentication to protect your web assets.


Comments
10:44 pm
When it comes to website security, it does not matter how powerful you are.
7:45 am
Actually, the truly powerful are bigger, juicier targets, so they're under more scrutiny and experience more attacks. But general security hygiene protects us all, no matter how powerful.
11:57 pm
Thank you - interesting; and an explanation I can understand :)
12:15 am
Wordfence the best plugin
1:58 am
Takeaway lesson #2: Trump should have used Wordpress :)
7:47 am
And, Wordfence!
Apparently, the administration is using WordPress on WhiteHouse.gov. But the campaign is not.
2:34 am
It's possible to de-anonymize the ip address of the site hidden behind cloudflare. So, origin server hacked probability is not so low.
2:41 am
WOW, Thank you for sharing, the question is are the hackers Russians, Iranians, Chinese or the domestic? were you able to trace the IPs? If I'm hacked the most important thing is from where the attack came from, I think is important to know from where in the world or State the attackers did this. Lesson Never use easy passwords use 2FA good idea. I am very happy with Wordfence, Thank you.
7:56 am
Thanks for the comment, Roberto! We did not have access to the site's log files or other artifacts, so we're limited to analyzing probable intrusion vectors only at this time. Law enforcement appears to be involved; we'll be following this story.
4:28 am
Excellent read. Shared.
5:53 am
Wordfence nailed it. 2F Auth is a must. It won't be long before I can use all of Wordfence products, but I know their cyber teams know the best logistics.
8:15 am
I had to laugh at some of the exposed Trump passwords. ;-) It pays to use long, complex and not easily guessed passwords, but yeah... 2FA is becoming more and more a necessity, even on less sensitive services!
8:31 am
Thanks for the post.
Note that Expression Engine is now open source: https://github.com/ExpressionEngine/ExpressionEngine
10:27 am
I just activated last Monday 2FA for all my websites. It asks an extra step to connect as admin, but considering the daily attacks on the websites, you really have to be careful.
So enable that 2FA via Wordfence. I fully agree.
9:52 pm
I'm going to agree with Kuba on the IP address. It doesn't take but a matter of minutes to find out an IP address.
As much of a pain in the butt it might be, always lock-down the admin login as hard as possible.
Those passwords! Seriously...smh
1:59 pm
For 3FA, I use Wordfence with 2FA and WPS Hide Login to move my WordPress default login URL to a secret URL.
3:09 pm
Thanks for the detailed explanation and heads up on website security. Am downloading word fence on all my website right away. Thanks again
2:53 pm
We can rule out hijacking the registrar and changing the nameservers. That would update the domain’s last updated data in the Whois, which currently displays June 29, 2020.